You don’t need to be a cybersecurity expert to lock down your WordPress site. With Cloudflare’s Web Application Firewall (WAF), you can block common threats before they even knock on your door. The trick? Setting the right rules and knowing which ones matter most.
In this guide, you’ll find the best WAF rules tailored for WordPress that you can use right away, plus a quick breakdown of how Cloudflare’s WAF works behind the scenes. You’ll also learn the difference between custom and managed rules, how to set them up, and how they fit into a broader WordPress security strategy, especially if you’re using FlyWP.
Let’s start with the basics with a quick definition of Cloudflare WAF. Once you’ve got the groundwork, we’ll move straight into real-world examples.
What Is Cloudflare WAF and How It Works
Cloudflare WAF (Web Application Firewall) is like a smart security guard for your WordPress site. It sits between your website and the internet, filtering out bad traffic before it reaches your server. Think of it as a protective shield that blocks hackers, spam bots, and harmful scripts, without slowing down real visitors. And the best part? You’re in control. You can create your own firewall rules based on:
- IP addresses
- Countries
- URLs or paths
- Request headers (like user agents)
- Rate limits (like how many hits per second)
When using Cloudflare to protect your WordPress site, you get two kinds of powerful security tools: Managed Rules and Custom Rules. Both rule types work together to give your site a solid layer of defense, smart defaults from Cloudflare, plus your own personal guardrails. They might sound similar, but they work very differently. Let’s break it down in the following section.
Custom Rules vs Managed WAF Rules: What’s the Difference?
Both managed and custom rules play a unique role in keeping security threats at bay. Understanding how they complement each other helps you build a defense that’s not just strong, but also smart. Know more from the comparison below.
Managed Rules: Cloudflare’s Built-In Rulesets
These are pre-made by Cloudflare’s security experts. They cover a wide range of known threats, like SQL injection, XSS, and attacks targeting WordPress. Cloudflare keeps these rules updated for you, so you don’t have to lift a finger. You’ll get protection against:
- OWASP Top 10 vulnerabilities (like XSS, SQLi, etc.)
- Specific CMS attacks (WordPress, Joomla, Magento…)
- Bad bots and scanners
- Common CVEs (known security holes in plugins/themes)
You don’t have to write these rules yourself. You just enable them.
Custom Rules: Your DIY Security Kit
These are the rules you have to create yourself. You can block traffic from certain countries, filter out sketchy bots, or protect specific files. It’s your call. Custom rules let you fine-tune your protection based on what your site needs. You can create rules like:
- Block access to
/wp-login.phpfrom certain countries - Rate-limit XML-RPC abuse
- Allow traffic only from your IP
- Challenge bots on specific paths
So, which one should you use? Short answer? Both. Use Managed Rules to cover your base and Custom Rules to fine-tune your defense. Here’s a quick table:
| Feature | Managed Rules | Custom Rules |
|---|---|---|
| Who writes it? | Cloudflare | You |
| Maintenance | Automatic updates | Manual |
| Use case | General threats | Specific threats |
| Ease of use | One-click enable | Rule builder |
| Flexibility | Limited customization | Full control |
Benefits of Applying Cloudflare WAF Rules
Why do WAF rules matter for WordPress? Because WordPress sites are a juicy target. Weak plugins, exposed login pages, XML-RPC abuse – hackers love those loopholes. Cloudflare WAF lets you close them fast, without breaking your site or slowing it down. Let’s have a quick look at the benefits of applying the best Cloudflare WAF rules for WordPress security:
1. Stops Hackers Before They Reach WordPress: Cloudflare blocks harmful traffic before it even touches your server. That means fewer chances for attacks like brute force logins, SQL injections, or plugin exploits.
2. Blocks Bad Bots and Spam: WAF rules help filter out bots pretending to be visitors. This cuts down on fake logins, comment spam, and scraping.
3. Improves Website Speed and Performance: By blocking useless or harmful traffic, your server doesn’t waste resources. Your real users get faster page loads and better performance.
4. Protects Sensitive Files: Certain WordPress files, like wp-config.php or .env, should never be accessible. WAF rules make sure they stay private even if someone tries to poke around.
5. Reduces Plugin Dependency: Why install five extra security plugins when Cloudflare can handle it at the edge? Fewer plugins mean less bloat and fewer things that can break.
6. Custom Defense for Your Needs: Whether you only allow logins from one country or want to block weird requests, custom WAF rules let you build protection that fits your setup.
7. Peace of Mind: Once your WAF rules are in place, they work silently in the background, blocking threats 24/7 so you can focus on running your site, not defending it.
Next, let’s talk about the must-have rules every WordPress site should enable – no fluff, just pure defense.
Best Cloudflare WAF Rules for WordPress Security

Keeping your WordPress site safe isn’t just about strong passwords and plugins. Most attacks happen before anyone even logs in – and that’s where Cloudflare’s Web Application Firewall (WAF) steps in. A mix of Cloudflare’s built-in Managed Rules and your own Custom Rules can block 95% of common threats before they reach your site. Let’s break the WAF rules down, one by one. The following guide combines the best of both worlds.
1. Block Access to wp-login.php from Other Countries
Type: Custom Rule
Why: If you only log in from one country, there’s no reason to let the rest of the world hit your login page. This shuts down thousands of brute-force attempts.
WAF Rules
- URI Path → contains →
/wp-login.php - Country → is not in → your country
Action: Block
Benefit: Stops bots from hammering your login form.
2. Block Access to xmlrpc.php
Type: Custom Rule
Why: This file is outdated and mostly used by bots to launch attacks like DDoS or brute force.
WAF Rules
- URI Path → equals →
/xmlrpc.php
Action: Block
Benefit: Cuts off a popular attack path.
3. Rate Limit Login Attempts
Type: Custom Rule
Why: Bots try hundreds of passwords in seconds. This rule slows them down and blocks them fast.
WAF Rules
- URI Path → contains →
/wp-login.php - Method → POST
Action: Rate Limit (e.g., 5 per minute), then JS Challenge or Block
Benefit: Protects your login page from brute-force bots.
4. Block Bad or Non-Browser User-Agents
Type: Custom Rule
Why: Bots often say they’re tools like curl or python – not real browsers. This helps you spot them easily.
WAF Rules
- User-Agent → contains →
curl,python,wget,scrapy,requests
Action: Block
Benefit: Keeps bad bots and scrapers out.
5. Block Access to Hidden or Sensitive Files
Type: Custom Rule
Why: Files like .git, .env, or even readme.html can expose secrets if left open.
WAF Rules
- URI Path → matches regex →
(?i).*\.git.*|.*\.env.*|.*readme\.html.*
Action: Block
Benefit: Hides sensitive dev files from prying eyes.
6. Block Access to wp-config.php
Type: Custom Rule
Why: This file holds your database info. If anyone sees it, they can take over your site.
WAF Rules
- URI Path → contains →
wp-config.php
Action: Block
Benefit: Locks down your most important config file.
7. Block SQL Injection Probes
Type: Managed Rule
Why: Some hackers try to sneak database commands into your URLs. Cloudflare’s managed rules detect this.
WAF Rules
- Use Cloudflare’s OWASP SQL Injection Rule Set
Action: Block
Benefit: Stops sneaky attacks before they reach your site.
8. Block XSS Attack Patterns
Type: Managed Rule
Why: Cross-site scripting attacks inject harmful scripts. Cloudflare’s XSS protection can sniff them out.
WAF Rules
- Use Cloudflare’s OWASP XSS Rule Set
Action: Block
Benefit: Protects your users from pop-up spam, hijacks, and worse.
9. Block Comment Spam Bots
Type: Custom Rule
Why: Spambots flood your comments with trash links. This rule cuts off their access.
WAF Rules
- URI Path → contains →
/wp-comments-post.php - User-Agent → contains →
bot,curl,python
Action: Block
Benefit: Keeps your comment section clean and human-only.
10. Block Requests With Empty User-Agent or Referrer
Type: Custom Rule
Why: Real browsers always say who they are. Bots don’t. If headers are empty, it’s probably bad.
WAF Rules
- User-Agent → equals →
"" - OR Referrer → equals →
""
Action: Block
Benefit: Filters out silent, stealthy bots.
11. Challenge Access to Plugin Folders
Type: Custom Rule
Why: Hackers scan plugin folders looking for outdated versions with known bugs.
WAF Rules
- URI Path → starts with →
/wp-content/plugins/
Action: JS Challenge
Benefit: Keeps bots away while real users pass through.
12. Challenge Long Query Strings
Type: Custom Rule
Why: Extra-long URLs are often used by scanners and hacking tools.
WAF Rules
- URI Query Length → greater than → 256
Action: JS Challenge
Benefit: Stops suspicious traffic without blocking humans.
How to Create WAF Rules in Cloudflare (Step-by-Step)
If you’re on the Cloudflare free plan, you can’t use all WAF rules. To unlock even basic WAF protection for your WordPress site, you’ll need Cloudflare’s paid plans. With the Pro plan, you get access to WAF with Managed Rulesets, including the OWASP Core Ruleset and WordPress-specific protections. You can also create basic Custom WAF Rules. Let’s learn: How to Create a Cloudflare Account and Add a Website.
What Plan Do You Need?
Not sure which Cloudflare plan fits your needs? This table breaks down what WAF features you get with each one.
| Plan | Managed Rules | Custom Rules |
|---|---|---|
| Free | Basic set | 5 rules max |
| Pro ($20/month) | Full rulesets (WordPress, OWASP) | 20 rules |
| Business ($200/month) | Advanced rules | 100+ rules, regex support |
Let’s set up your WAF rules and activate them. Follow the steps below to get your custom protections running in minutes.
Part 1: How to Enable Cloudflare Managed Rules
Think of these as Cloudflare’s built-in defenses. They’re maintained and updated regularly to guard against threats like SQL injections, cross-site scripting (XSS), and known WordPress exploits.
Note: Some managed rules, especially those tagged “WordPress” are only available on Pro plans or higher.
Log in to Cloudflare: Go to dash.cloudflare.com. Select your website.
Go to the WAF Panel: In the sidebar, click Security. Then choose WAF (Web Application Firewall).
Open the “Managed Rules” Tab: At the top, click the Managed Rules tab. You’ll now see a list of available rule sets.
Enable These Core Rulesets:
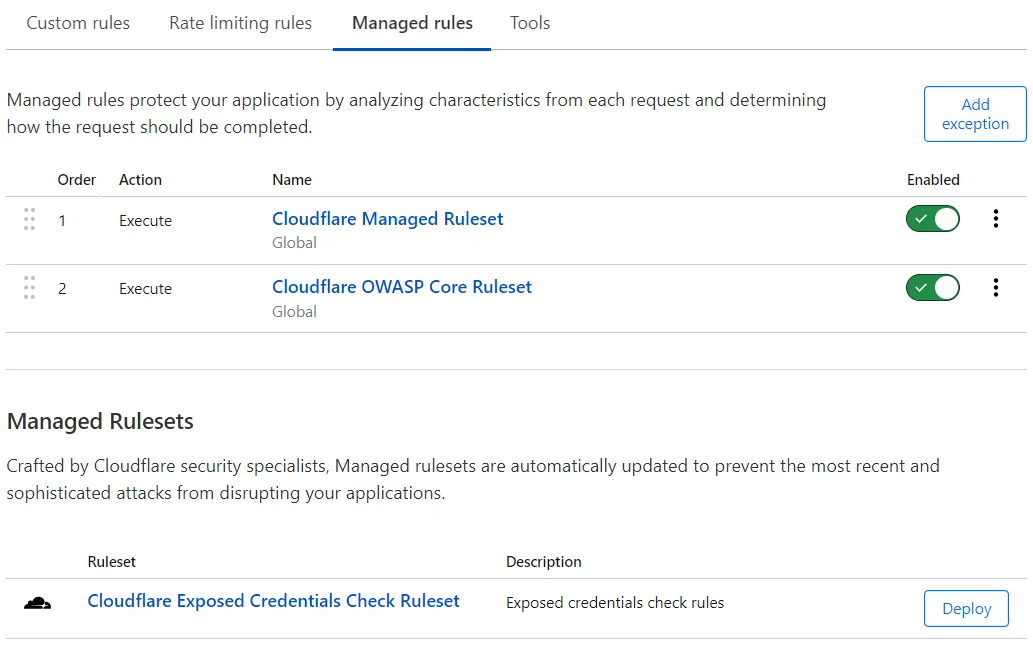
| Ruleset | Purpose |
|---|---|
| Cloudflare Managed Ruleset | Blocks threats like SQLi, XSS, and bots. |
| OWASP ModSecurity Core Ruleset (Pro+) | Provides industry-standard protection. |
Turn on WordPress-Specific Rules (Pro Plan Only): Click into the Cloudflare Managed Ruleset. Use the search or tag filter to find rules tagged “WordPress”. Enable them. Set actions to Challenge or Block.
Adjust Individual Rules (Optional): Click on a ruleset name. View individual rules and tweak actions as needed. Actions include:
- Log – Just records the request.
- Challenge – CAPTCHA test.
- Block – Completely blocks.
Click “Deploy” or “Save”: Done! Your managed rules are live.
Part 2: How to Create Custom WAF Rules
Custom rules are like your own digital guard dogs. They let you stop specific threats that managed rules might overlook—especially useful for blocking brute-force login attempts, file exploits, or bad bots.
Open the Custom Rules Tab: Under your site’s dashboard, go to: Security → WAF → Custom Rules
Click “Create Rule”: Hit the blue Create Rule button.
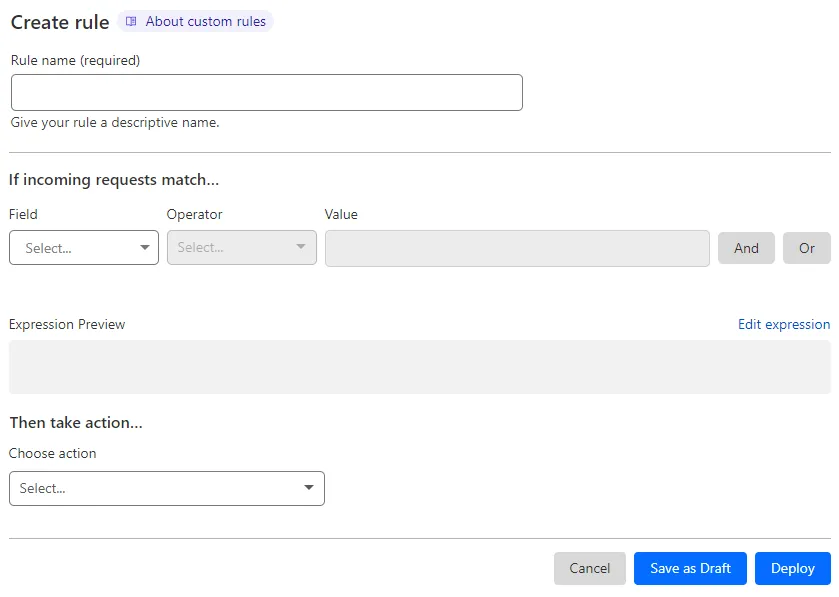
Give It a Clear Name: Something like Block wp-login outside US works fine.
Set Conditions Using the Expression Builder: Use the dropdowns to build rules.
Choose an Action: Pick what happens when the rule matches:
- Block – Stops them cold.
- Challenge – CAPTCHA test.
- JS Challenge – JavaScript browser check.
- Log – Record but don’t block.
Deploy the Rule: Click Deploy to activate it.
Ready-to-Use Cloudflare WAF Rules for WordPress Security
Want to skip the technical guesswork? These ready-made Cloudflare WAF rules are perfect for blocking common WordPress threats. Just copy, paste, and tweak as needed.
1. Block wp-login.php from outside the US
WAF Rule:
(http.request.uri.path contains "wp-login.php" and not ip.geoip.country in {"US"})Action: Block
2. Block wp-admin from outside the US
WAF Rule:
(http.request.uri.path contains "/wp-admin" and not ip.geoip.country in {"US"})Action: Block
3. Block access to xmlrpc.php
WAF Rule:
(http.request.uri.path contains "/xmlrpc.php")Action: Block
4. Block bad bots by User-Agent
WAF Rule:
(http.user_agent contains "Xenu") or
(http.user_agent contains "MJ12bot") or
(http.user_agent contains "Alexibot") or
(http.user_agent contains "SurveyBot") or
(http.user_agent contains "rogerbot")Action: Block
5. Block AI scrapers
WAF Rule:
(cf.verified_bot_category eq "AI Crawler")Action: Block
May affect SEO if you block legitimate AI crawlers like Perplexity or ChatGPT.
6. Block empty User-Agent or Referrer
WAF Rule:
(http.user_agent eq "") or (http.referer eq "")Action: Block
7. Block access to sensitive files
WAF Rule:
(http.request.uri.path contains "/.env") or
(http.request.uri.path contains "/wp-config.php") or
(http.request.uri.path contains "/backup.zip")Action: Block
Important Note: Use VPNs or browser extensions to simulate different countries and devices. Watch the firewall logs in Cloudflare for blocked or challenged requests.
How FlyWP Secures Your WordPress Site from Day One
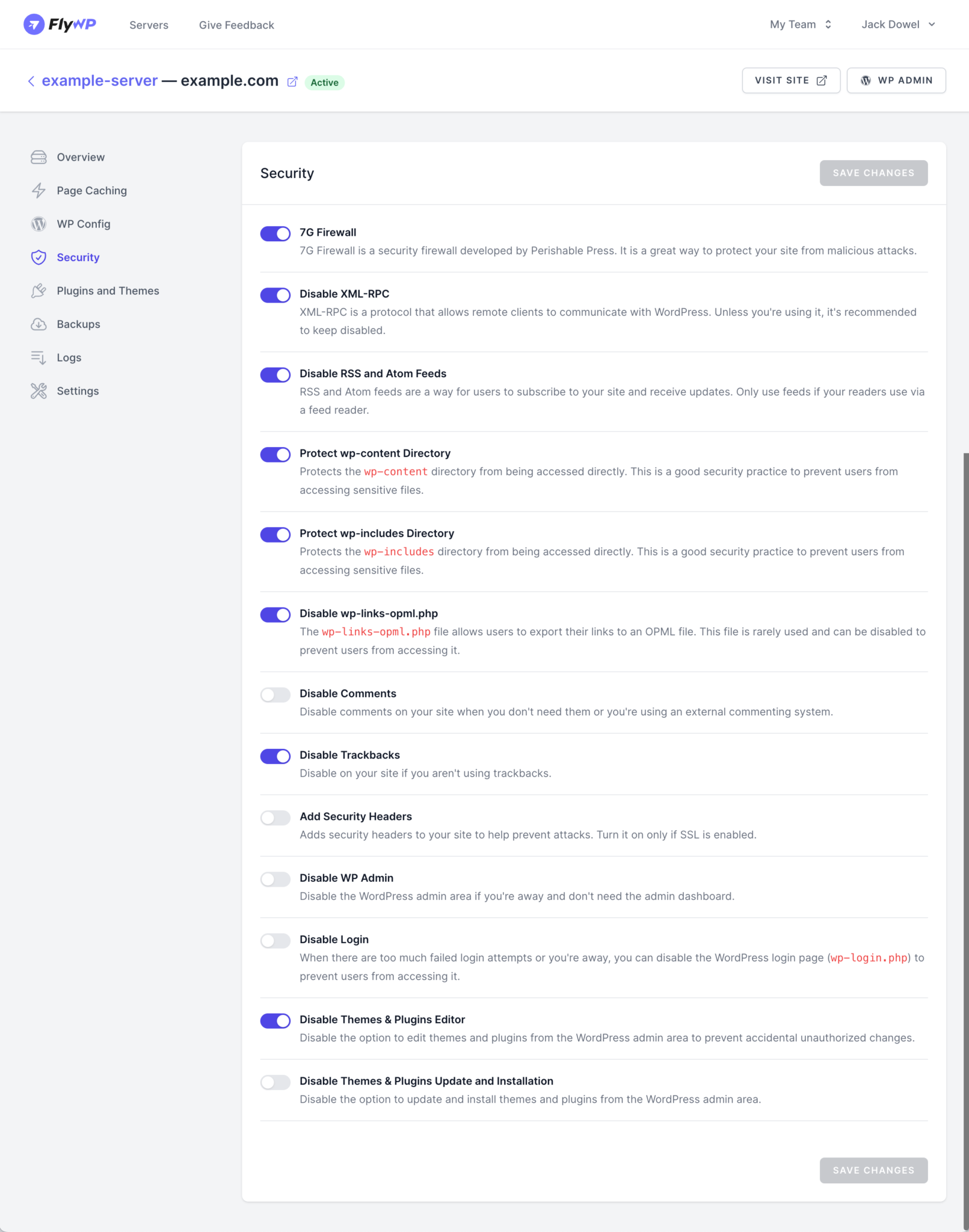
Security isn’t just a feature at FlyWP, it’s the foundation. The moment you spin up a new WordPress site, FlyWP goes to work behind the scenes. It handles essentials like 7G Firewall, Docker-based isolation, and optimized Nginx rules. And if you’re a hands-on kind of user, there are tools to fine-tune protection even further. Here’s a quick glimpse of the default security measures FlyWP offers:
| Feature | Description |
|---|---|
| 7G Firewall Integration | Lightweight firewall by Perishable Press that blocks malicious requests and common attack vectors. |
| Automatic Firewall Deployment | Instantly applies pre-optimized firewall rules for WordPress when a site is created. |
| Cloudflare Integration | Lets you manage DNS, cache, and security rules from the FlyWP dashboard, with automatic syncing. |
| Optimized Nginx Configuration | Uses Nginx as a Web Application Firewall (WAF) to block threats at the server level. |
| XML-RPC Disable Option | Option to disable XML-RPC, a common target for brute-force and DDoS attacks. |
| Docker-Based Site Isolation | Each site runs in its own Docker container, isolating environments and reducing cross-site risk. |
| Regular Updates & Monitoring | Helps keep WordPress, plugins, and themes updated to patch known security issues. |
When you pair Cloudflare’s WAF with FlyWP’s built-in security tools, you’re actually building multiple layers of defense. On top of these security tools, seamless Cloudflare integration lets you manage DNS, cache, and security rules without lifting a finger.
Cloudflare WAF with FlyWP: A Perfect Match for WordPress Security
FlyWP integrates with Cloudflare to add extra layers of security for your sites. Cloudflare’s WAF protects your site at the edge, while FlyWP locks things down at the server level. When used together, they create a strong defense, stopping threats before they ever touch your WordPress install.
FlyWP manages performance, PHP versions, server updates, and firewall security features. But when it comes to blocking threats before they reach your server, that’s where Cloudflare WAF shines. Here’s why combining them gives you the best of both worlds:
- Cloudflare blocks threats before they hit your FlyWP-managed server.
- FlyWP keeps your server lean and optimized with Nginx/OpenLiteSpeed, security, and PHP tweaks.
- Together, they reduce server load, boost security, and improve site speed.
FlyWP’s built-in security features perfectly complement your Cloudflare WAF rules. The result? A safer, faster, and smarter WordPress experience without the headaches. Cloudflare WAF sits in front of your domain, so all these custom and managed rules work out of the box, whether you’re hosting a WooCommerce store, a membership site, or a personal blog. This combination is what serious WordPress site owners should aim for: a lightweight server stack and intelligent edge security.
